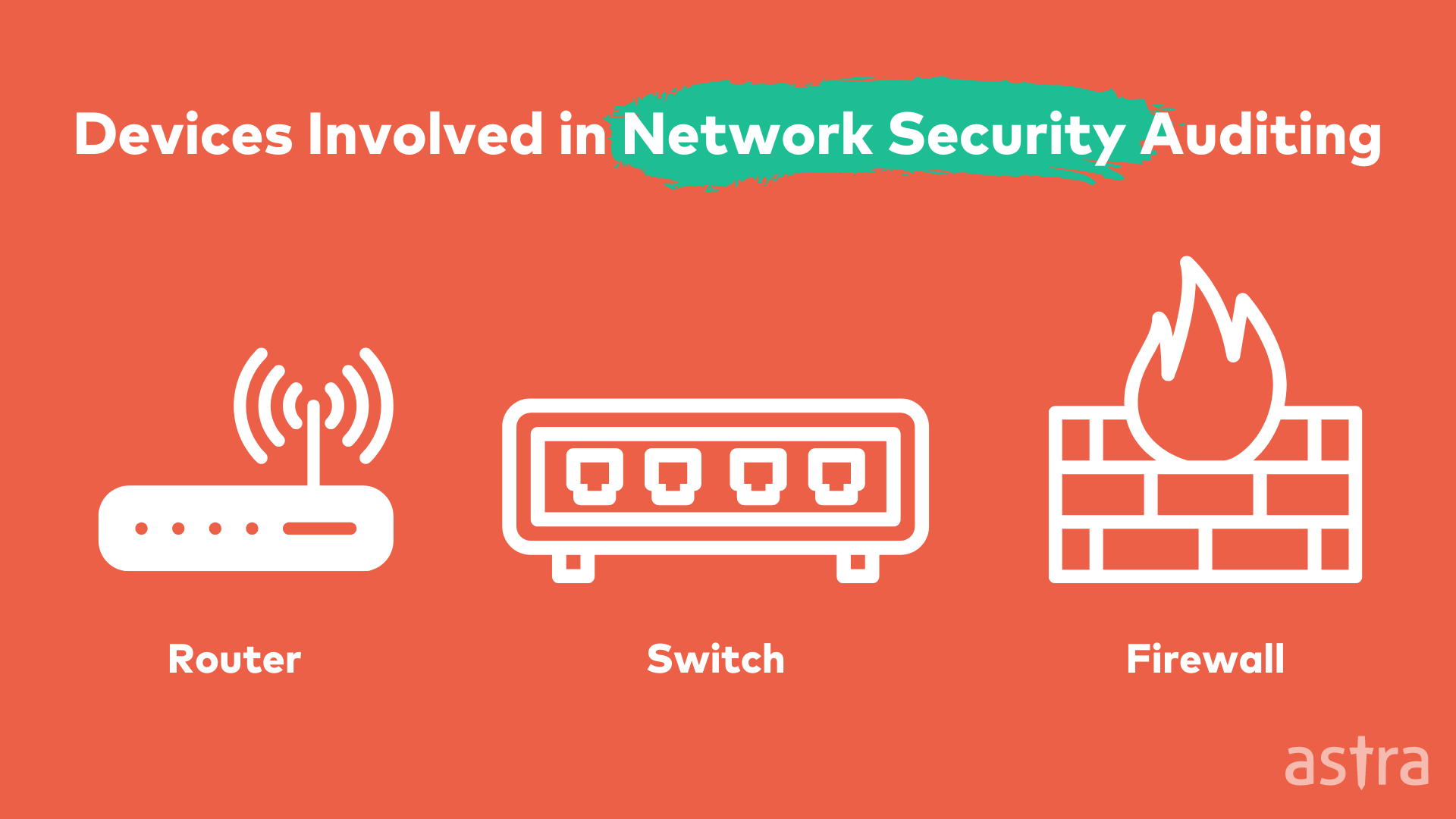
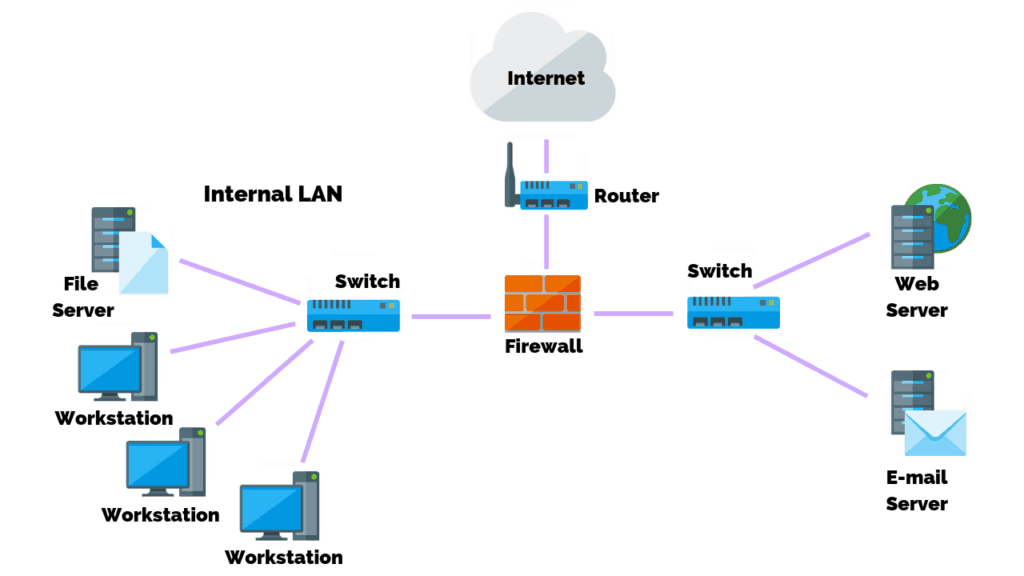
Switch Security: Management and Implementation (2.2) > Cisco Networking Academy's Introduction to Basic Switching Concepts and Configuration | Cisco Press
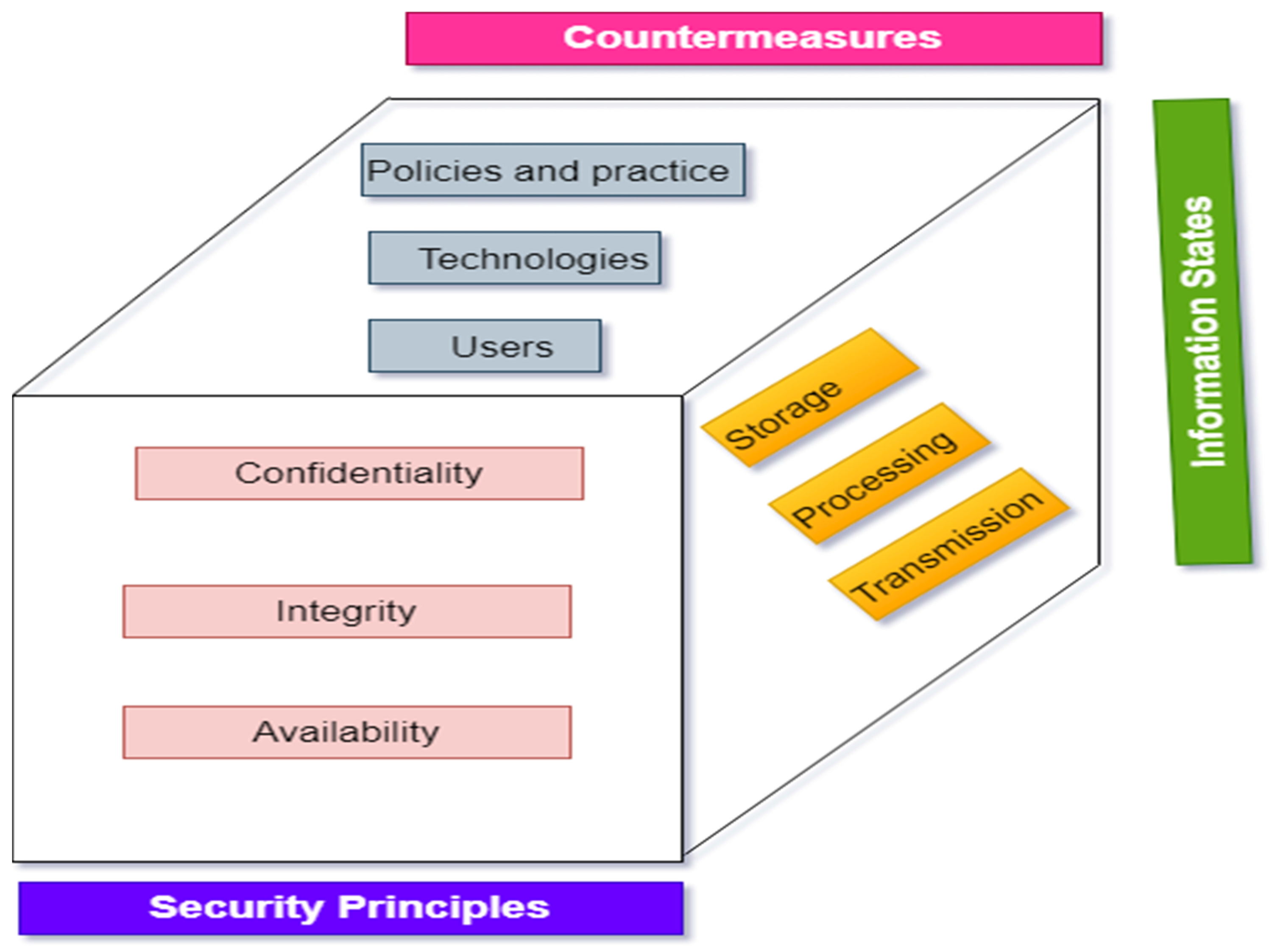
Electronics | Free Full-Text | A Comprehensive Review of Cyber Security Vulnerabilities, Threats, Attacks, and Solutions

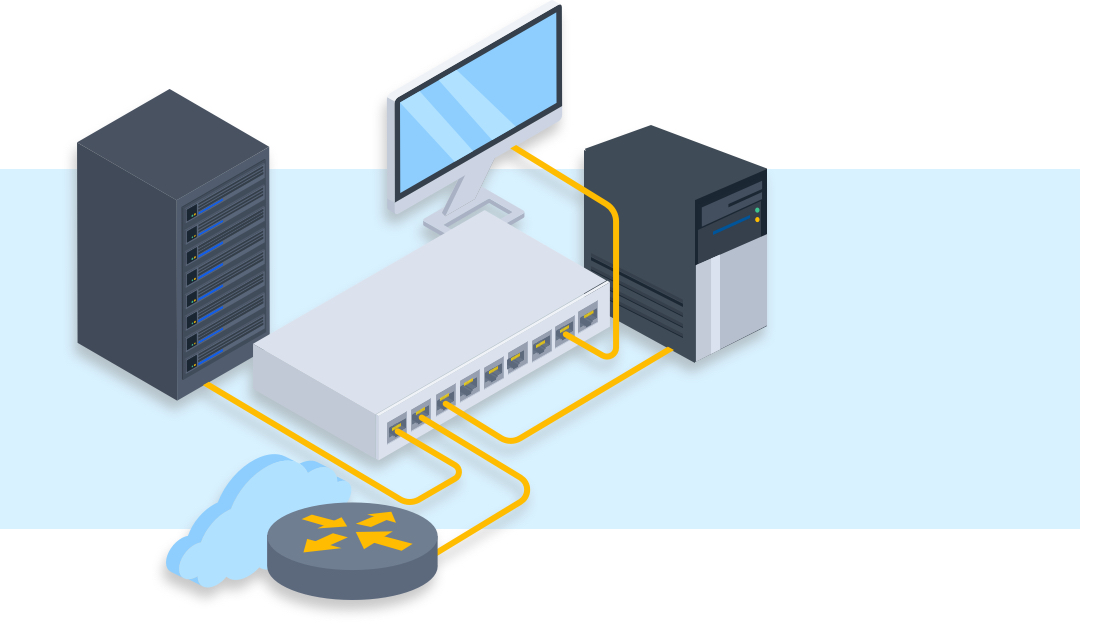
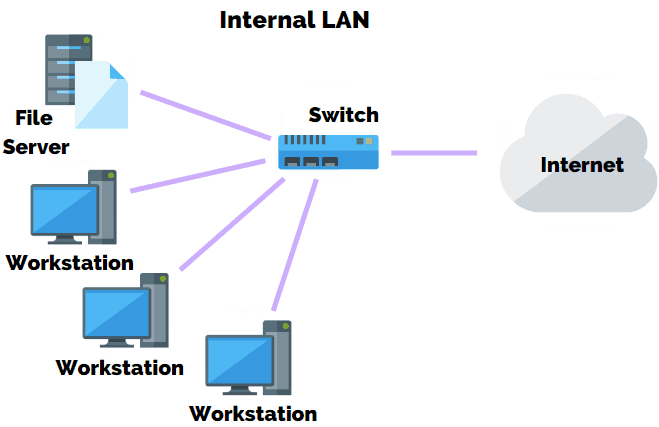
Switch Security: Management and Implementation (2.2) > Cisco Networking Academy's Introduction to Basic Switching Concepts and Configuration | Cisco Press

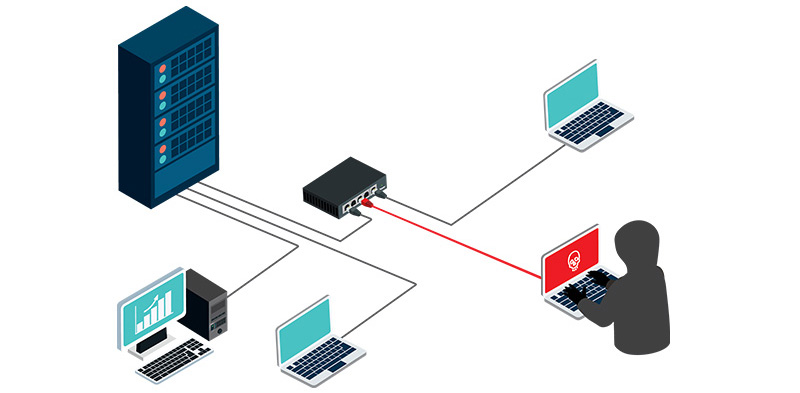
Know Cyber Network Security | How to prevent Network Attacks | Types of Network Attacks | EC-Council